With the adoption of remote working comes a plethora of new security considerations; chief among them is the question of how an organisation secures its network. Traditional access controls are simply not designed to cope with such a rapidly evolving threat landscape, especially over a dynamic, cloud-based, and ever-expanding network perimeter. As a result, as applications and resources migrate to the cloud, Secure Access Service Edge (SASE) is quickly transitioning from a cloud-based alternative to the traditional centralised network infrastructure, to an essential model in network security. Typically, the most effective means of securing anything is to completely hide its existence from potential attackers, but how do you achieve that with a cloud-based or hybrid network?
The answer begins with the principle of Zero Trust Network Access (ZTNA); broadly speaking, the principle that ‘no user—human or machine—should be automatically granted access to anything’[i]. Initially, this may appear to be an extreme measure, but this model greatly strengthens an organisation’s security posture and is rapidly becoming an industry standard, with two thirds of organisations as of 2020 reporting to expect their expanded remote working policies to remain in place long-term or even permanently[ii]. Again, however, traditional network perimeters aren’t designed with this approach in mind; they are static and largely work from the principle of a physical perimeter with a centralised data source, a concept which is rapidly becoming obsolete.
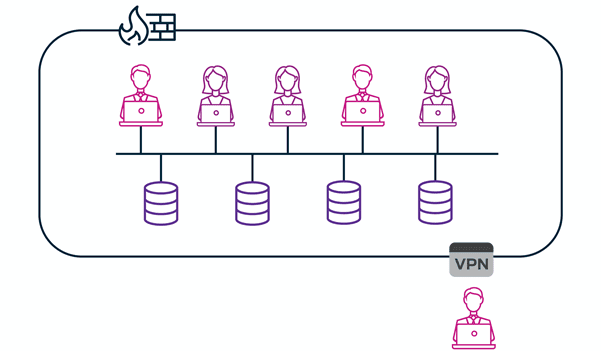
Traditional network access solutions, such as VPNs and firewalls, are not flexible enough to effectively function remotely, or within the principle of ZTNA.
For more information on ZTNA, take a look at the Gartner 2020 Zero Trust Network Access Market Guide.
One of the most effective first steps in solving these problems is to deploy a software-defined perimeter.
A software-defined perimeter (SDP) is a boundary that completely cloaks an infrastructure from outside entities; only authorised users can see and access the network and any assets contained within it. The same verification measures apply to devices as well as users themselves, effectively closing off another avenue of attack via stolen or compromised credentials. By default, an SDP should operate hand-in-hand with a ZTNA policy; users and devices are never automatically assumed to be trustworthy and are only permitted to see and access the infrastructure once their identity is verified. On top of the security advantages provided by the ZTNA principle, this single framework is the base model applied to all users and devices, resulting in greatly simplified and streamlined network policy.
In addition to this, SDPs operate on a granular level; depending on context, different users can be granted different levels of access, or access to different resources, granting a greater degree of flexibility than a traditional VPN. Additionally, because an SDP is based on software rather than hardware, it can operate on a SASE, and as such, there is no requirement to route traffic through a data centre; it can be deployed anywhere and scales easily to connect users and devices in any location depending on an organisation’s requirements, regardless of whether your environment is in the cloud, on-premises, or a hybrid of the two.
So how does it work?
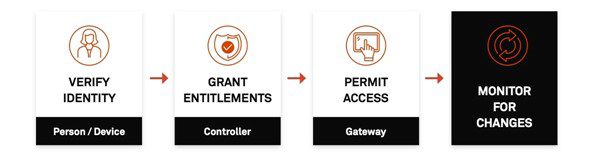
Unlike a standard VPN, which connects a user to a larger, shared network, an SDP uses single-packet authorisation (SPA) to establish an individual (or ‘Segment of One’) network between a device and a server that is invisible and inaccessible to anyone else. This connection is only allowed after both the user’s identity and the state of the device in use is verified, and it only allows access to applications and assets for which the user is approved. This is managed by a controller, which is an engine that checks policies, conditions and entitlements for all users and devices, and a gateway, which enforces the decision made by the controller. In addition, this process is automated, creating a dynamic network that continuously monitors for metadata and context changes that would affect user entitlements and adapts according to its environment.
How do you get started?
When it comes to secure access solutions, Appgate SDP is an industry leader; their mission is to improve the whole cybersecurity landscape by making their solutions simple for the user but impenetrable for potential attackers. Their SDP architecture aligns completely with the ZTNA principle, and allows organisations to reduce complexity and streamline automation while strengthening security, leading to a seamless, secure user experience.
Want to find out more? Take a look at this video to learn more about Appgate SDP:
References
- Scheels, C. (2021) ‘GUIDE TO ZTNA, PART 1: WHAT IS ZTNA? ZTNA DEFINITION AND OVERVIEW’ https://www.appgate.com/blog/ztna-definition
- Crawford, S.; Bekker, G.; Montenegro, F.; Sherrill, A.; Hanselman, E. (2020) ‘SASE, ZTNA and XDR: Three security trends catalyzed by the impact of 2020’ https://d3aafpijpsak2t.cloudfront.net/docs/Analyst-Reports/451_Reprint_SASE_ZTNA_XDR_19AUG20.pdf?mtime=20200910114114&focal=none&utm_source=website&utm_campaign=451_report_sase_ztna_xdr
- https://www.appgate.com/software-defined-perimeter
Other recent news

SenseOn Partners With Kite Distribution to Boost UK Channel Growth in 2025

Kite & Cyberbit Forge Strategic Alliance

Simplifying the Stack

Kite & Uptycs Announce Strategic Partnership

