Space: The final frontier…
Immortal words first uttered by William Shatner on September 8th, 1966, in the opening credits of a show that would spawn one of the most prolific science-fiction franchises in history. That’s right; we’re doing a Star Trek blog. Just like the average Starfleet ship, a company’s network is a point of huge strategic value, and the cost of a security breach is potentially disastrous. So how can you utilise MSP network security offerings to make the ship impenetrable to intruders, but still accessible for approved users? Let’s take a look.
Bitdefender
Let’s start with the perimeter of your network. This isn’t exclusive to Star Trek; no ship in any science-fiction show would have lasted very long without some means of protecting its hull, whether that was through armour or shielding or some combination of the two. We’re picking on the shields in Star Trek because, as well as absorbing damage from phasers and disruptors and whatever other variants on ‘like lasers and torpedoes, but in space’ the writers care to come up with, they have another key property; transporters can’t beam matter through them. This means that they can function as an effective barrier against covert intrusion as well as an overt attack (barring interference from near-omnipotent super beings putting humanity on trial or cybernetic collectives bent on assimilating all life in the universe, but if things get to that point, we’ve got bigger problems).
Now, that’s all very well for the Enterprise, but how do you apply a similar concept to your network? Bitdefender’s GravityZone offers Endpoint Security and Security for Virtualised Environments, leveraging features such as mature AI and advanced risk analytics to provide robust protection and strengthened security across your entire network. There are also a number of optional add-ons, including Full Disk Encryption, Advanced Threat Response and Email Security, allowing you to strengthen your defences still further, all in one easy to use platform.
Bitdefender GravityZone Cloud MSP Security Suite
Entrust
Now, you can have shields up the whole time, but eventually, you’ll run into the problem of how do you let someone on board who is approved? In the past, the go-to solution would have been passwords, but that isn’t without flaws.
Passwords are a lot like the autodestruct codes used on the Enterprise; they run anywhere from memorable but concerningly simplistic, to secure but too complex for any human to reasonably remember, and there’s no way to really guarantee that you can hit the happy medium between the two. On top of that, the sheer number of applications requiring a password has increased to the point where the whole concept is rapidly becoming impractical. In the absence of a better solution, they’ll do the job to a point, which is why they’ve been the primary means of access management for so long, but they’re neither as secure nor as user-friendly as they should be, and better solutions do now exist.
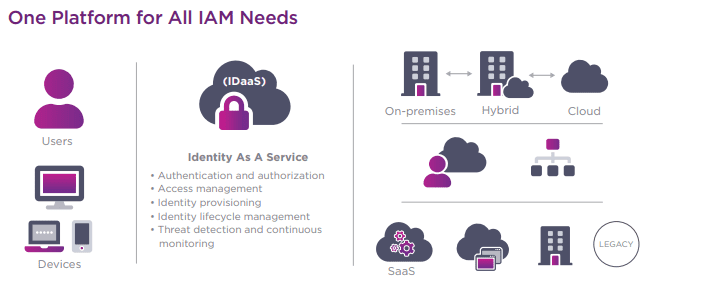
Entrust provides an extensive array of these solutions. As a company, they have been operating in the cybersecurity space for over fifty years, securing everything from debit and credit card purchases to networks and devices. Entrust Identity as a Service consolidates multiple authentication solutions into one platform, including single sign-on, credential-based passwordless access, adaptive risk-based access, and industry-leading multi-factor authentication, creating a frictionless login experience whilst making sure that your network remains secure. Best of all, it’s flexible; you can deploy it in a cloud, on-premises, or hybrid environment – whichever suits you.
Learn more about Entrust’s MSP programme here:
Become a Managed Service Provider | Entrust
Appgate
If you’ve watched more than one episode of any series of Star Trek, you probably know that just because something’s managed to get onto the ship, that doesn’t mean it’s necessarily friendly. Even leaving aside intruders and dignitaries who almost invariably turn out to be trying to take over or destroy the ship, there’s also the possibility of someone on the inside being compromised. Case in point: once could be pure misfortune, but after the second or third instance of your android crewmember getting his programming hacked and commandeering the ship in less than ten minutes, perhaps you ought to start looking into a more stringent internal security policy. The point is, just because a device or user has the credentials to access your network, that doesn’t mean you can assume that they will continue to be trustworthy once they’re in there.
So how do you allow someone to move around your network without allowing them to see or access the things you don’t want them to? Enter Appgate, an industry leader in secure access solutions. Appgate SDP (software-defined perimeter) offers a boundary that not only cloaks a network infrastructure from the outside, but also creates an individual network connection between a device and a server, which is completely invisible and inaccessible from the outside. On top of that, the connection is dynamic, adapting to changing policies, conditions, and entitlements for all users, and will only allow access to applications and assets for which the user is approved.
Appgate | Zero Trust Network Access (ZTNA) MSP Partner Program
Conclusion
The outlook of all this is, from a security standpoint, pretty optimistic. As we edge closer to the 23rd century, when ships like the Enterprise should be becoming a reality (Back to the Future let us down on the hoverboard front, but we can still hold out hope for warp drive), we already have the tools available to us to create a network environment that is, in many respects, more secure than a starship.
Want to learn more about our MSP offerings, or just fancy a drink and a chat with us? We don’t have a Galaxy-class starship, but we are on board the Sunborn Yacht on the 22nd June for our Infosec #CyBeer Aftershow; register below to pre-book your ticket:
Other recent news

SenseOn Partners With Kite Distribution to Boost UK Channel Growth in 2025

Kite & Cyberbit Forge Strategic Alliance

Simplifying the Stack

Kite & Uptycs Announce Strategic Partnership

