Public Key Infrastructure.
Odds are good that a lot of people, upon reading those three words, have either checked out mentally, or started hammering the ‘Back’ button with the kind of panicked urgency usually reserved for the first day back at work after a holiday – the kind where you set your alarm with the best of intentions, but still manage to sleep through not only that, but also the three other alarms you set.
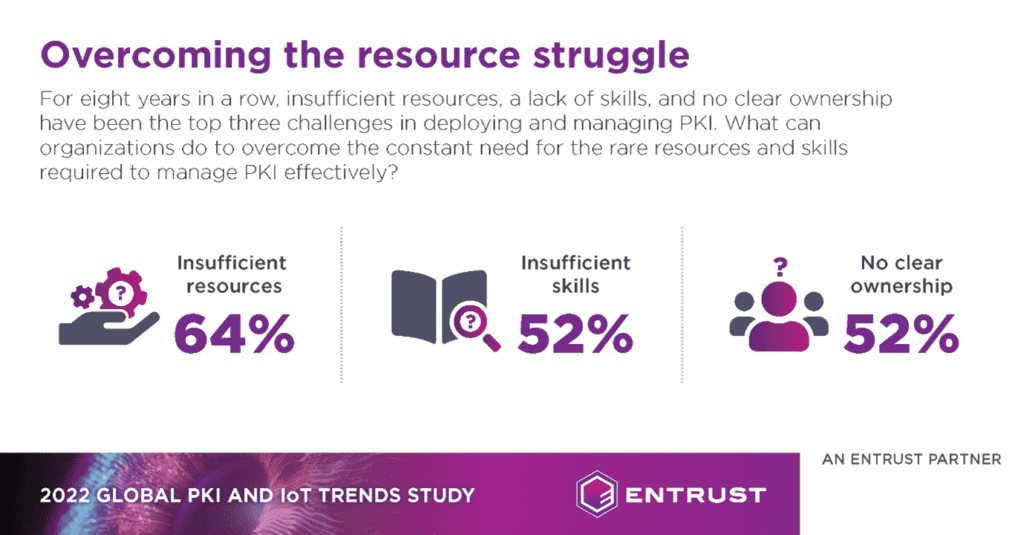
In all honesty, we can’t blame those people. PKI is a notoriously complex subject, both to understand and to explain – there isn’t really a handy metaphor that can neatly sum up the concept. In fact, the Ponemon Institute’s Global PKI and IoT Trends Study, sponsored by Entrust, consistently lists a lack of sufficient skills as one of the top three challenges of deploying and managing PKI, with the number of respondents reporting this challenge actually increasing to 52% in 2022, up from 46% in 2021.[1]
The problem is that as increased use cases of the cloud and IoT add more devices and more layers of complexity to the IT landscape, achieving PKI maturity has become more important than ever. Avoiding the subject isn’t really feasible anymore. Public key infrastructure is as powerful as it is complicated, and even a rudimentary understanding can make a huge difference when it comes to taking full advantage of its capabilities.
So, let’s put a pin in the infrastructure part for a moment. We can break PKI down into two main components.
Keys
The first component is keys. There are two types of keys: synchronous and asynchronous. A synchronous key can both encrypt and decrypt a piece of data. The advantage of a synchronous key is that it’s quick and can encrypt or decrypt large amounts of data at once. The problem is that it’s not especially secure. If that key is in some way compromised, then the door is open to compromise the whole organisation.
Asynchronous keys work in pairs; a private key which is stored securely by the information’s recipient, usually using an HSM, and is never made publicly available, and a public key which is more freely available. Only the private key can decrypt data encrypted by the public key; in effect, the two keys work together to make sure that only the intended recipient can see the information being sent. The disadvantage of this type of key is that it takes longer to encrypt and decrypt large amounts of data.
Trust
The second key component of PKI is trust. This is what gives credibility to the whole concept of a private key and ties the whole infrastructure together. In an asynchronous key pair, a trusted authority issues a tamper-evident digital certificate to the private key, which verifies all aspects of the certificate holder (name, email address, etc.). The public key is rarely issued its own certificate but is instead trusted by its association with the private key. Conceptually, it’s similar to a passport, where foreign governments trust the issuing country’s government, which trusts the issuing body verifying the information provided by the passport holder.
These two components form the foundation of PKI, but the real power lies in how they can interact. For example, since a synchronous key is a relatively small information string, a public asynchronous key can easily encrypt it. This is the basis of SSL security, a vital part of securing sensitive data used in online banking and ecommerce.
If you’re still here, congratulations. This is by no means a comprehensive explanation of PKI, but we really hope that we’ve managed to help untangle at least the fundamental aspects of what must be one of the most multi-layered and, frankly, intimidating concepts in cybersecurity.
Interested in learning more about the findings from the 2022 Global PKI and IoT Trends Study? Download the full report here:
[1] 2022 Global PKI and IoT Trends Study (sponsored by Entrust), Ponemon Institute, November 2022
Other recent news

SenseOn Partners With Kite Distribution to Boost UK Channel Growth in 2025

Kite & Cyberbit Forge Strategic Alliance

Simplifying the Stack

Kite & Uptycs Announce Strategic Partnership

